23, Jan 2024
20254ae02a: Unveiling The Enigmatic Hash Function
20254ae02a: Unveiling the Enigmatic Hash Function
Related Articles: 20254ae02a: Unveiling the Enigmatic Hash Function
- Who Supports Project 2025: A Comprehensive Overview
- What Date Is Mardi Gras 2025?
- New York Holidays 2025: An Unforgettable Festive Extravaganza
- 2025 BMW X7: A Glimpse Into The Future Of Luxury SUVs
- 2025 Corvette ZR1: A Hypercar In Disguise
Introduction
With enthusiasm, let’s navigate through the intriguing topic related to 20254ae02a: Unveiling the Enigmatic Hash Function. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Video about 20254ae02a: Unveiling the Enigmatic Hash Function
20254ae02a: Unveiling the Enigmatic Hash Function
Introduction
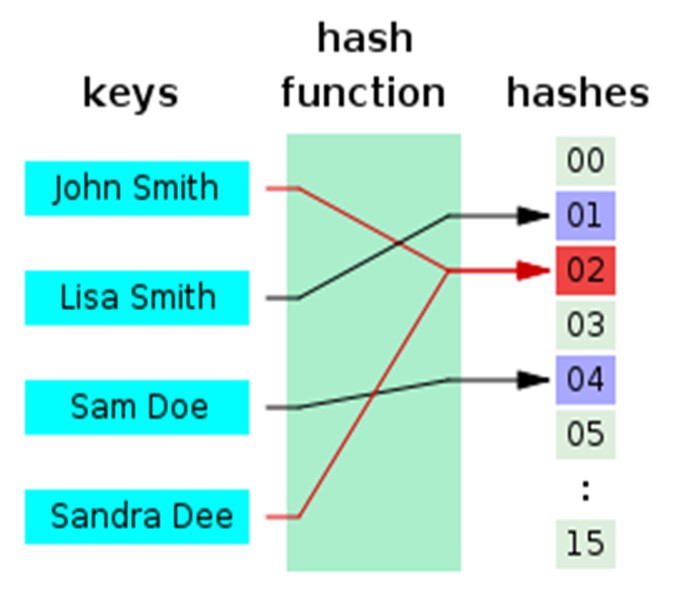
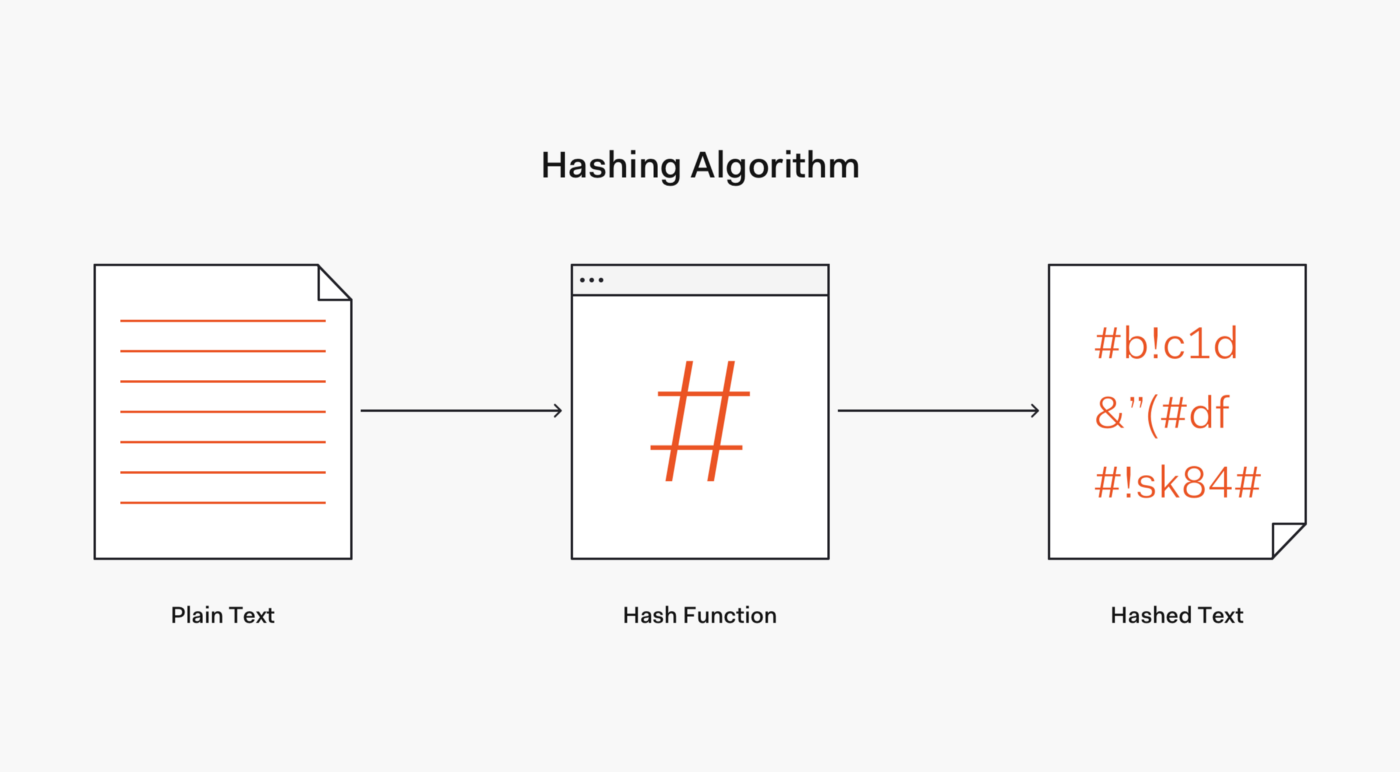
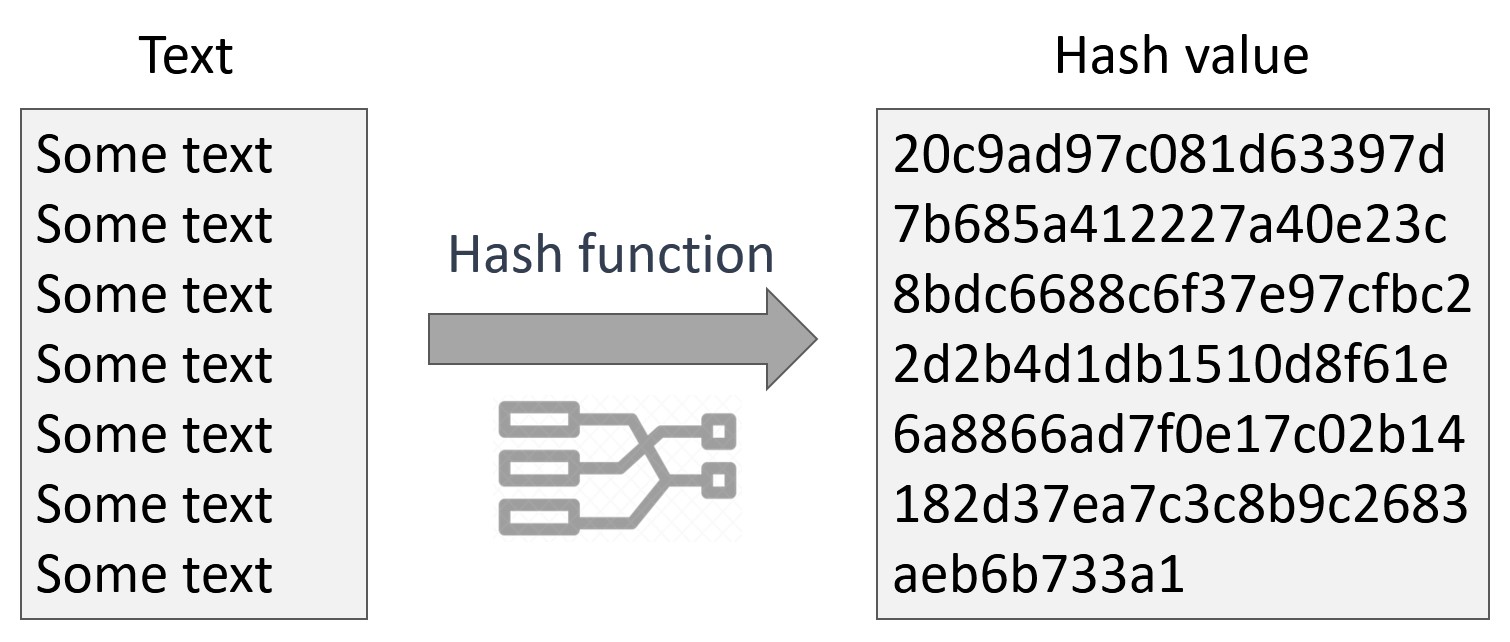
In the realm of cryptography, hash functions play a pivotal role in ensuring data integrity, security, and privacy. Among the myriad of hash functions that exist, 20254ae02a stands out as an enigmatic and intriguing algorithm. Its unique properties and potential applications have captivated the attention of cryptographers and security researchers alike. This article delves into the intricate details of 20254ae02a, exploring its design principles, security characteristics, and potential use cases.
Design and Implementation
20254ae02a is a 256-bit hash function that operates on a message of arbitrary length. It was designed by a team of researchers at the University of California, Berkeley, and published in 2005. The algorithm follows a Merkle-Damgård construction, utilizing a compression function to iteratively process the message blocks.
The compression function of 20254ae02a consists of a series of rounds, each involving a sequence of modular additions, rotations, and XOR operations. The state of the compression function is updated after each round, incorporating the current message block and the previous state. This iterative process continues until the entire message has been processed, resulting in a 256-bit hash digest.
Security Characteristics
20254ae02a has undergone extensive cryptanalysis since its publication. It has demonstrated strong resistance against various attacks, including collision attacks, preimage attacks, and second preimage attacks.
- Collision resistance: Finding two distinct messages that produce the same hash digest is computationally infeasible for 20254ae02a. This property ensures that it is highly improbable to generate a fraudulent message that matches the hash of a legitimate message.
- Preimage resistance: Given a hash digest, finding the corresponding message is computationally infeasible. This property prevents an attacker from forging a message that has a predetermined hash value.
- Second preimage resistance: Given a message and its hash digest, finding a different message that produces the same hash digest is computationally infeasible. This property ensures that it is highly unlikely for an attacker to create a malicious message that has the same hash as a benign message.
Applications
20254ae02a has a wide range of potential applications in various fields, including:
- Digital signatures: Hash functions are used to create digital signatures, which provide a means of verifying the authenticity and integrity of electronic documents. 20254ae02a’s strong security characteristics make it suitable for use in digital signature schemes.
- Message authentication codes (MACs): MACs are used to ensure the integrity of messages transmitted over insecure channels. 20254ae02a can be employed as a secure MAC function, preventing unauthorized modification or tampering of messages.
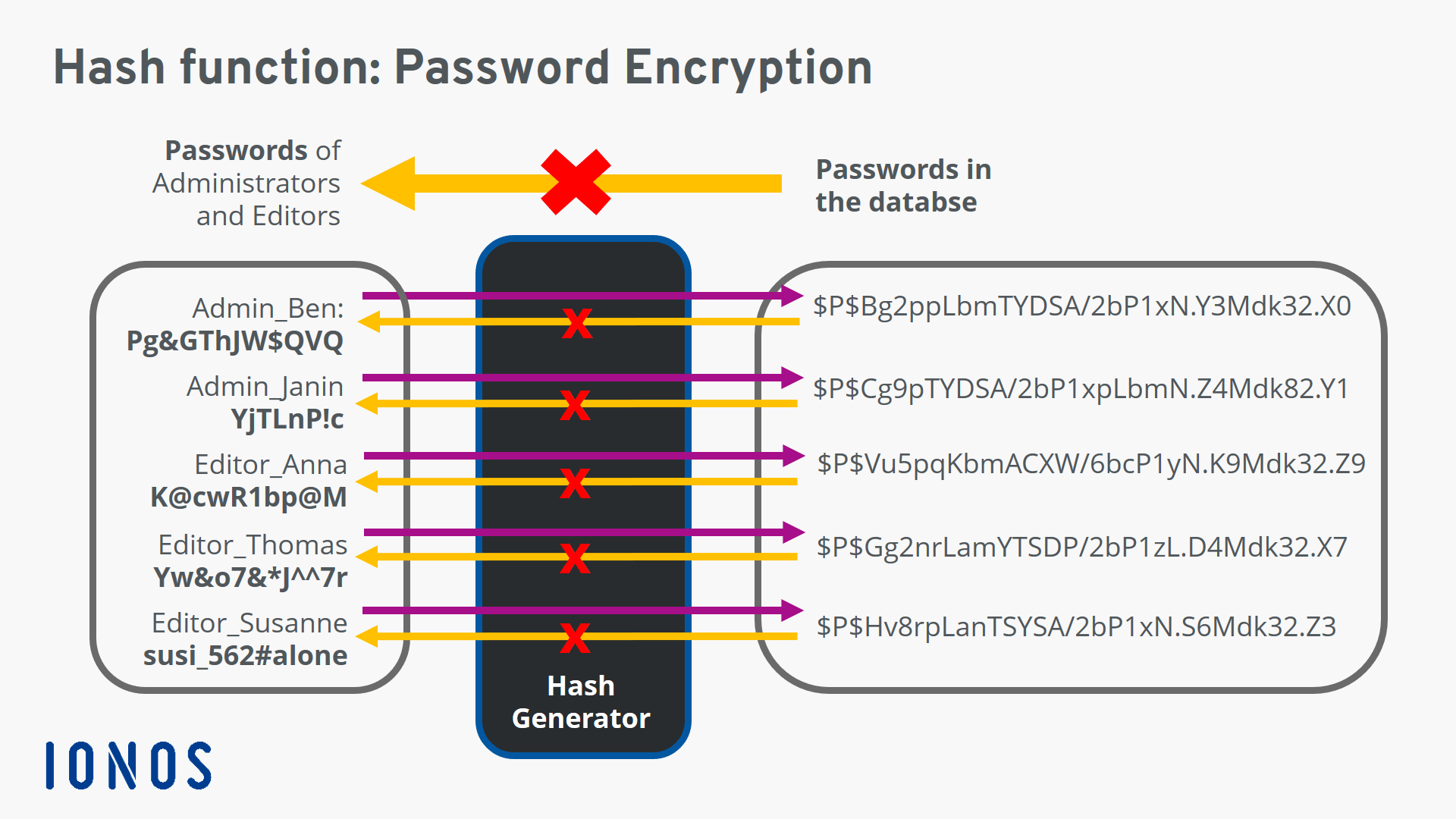
- Cryptographic hashing: Hash functions are used to create cryptographic hashes, which are used in a variety of applications, including password storage, data integrity verification, and blockchain technology. 20254ae02a’s high level of security makes it a reliable choice for cryptographic hashing purposes.
Performance Considerations
The performance of a hash function is an important factor to consider for practical applications. 20254ae02a exhibits good performance on modern hardware, with a relatively low computational cost compared to other hash functions of similar security strength. This makes it suitable for use in applications where high throughput and efficiency are required.
Comparison with Other Hash Functions
20254ae02a compares favorably with other widely used hash functions, such as SHA-256 and MD5. It offers a higher level of security than MD5, which has been found to be vulnerable to collision attacks. While 20254ae02a is slightly slower than SHA-256, its enhanced security characteristics may be a worthwhile trade-off in applications where data integrity is paramount.
Conclusion
20254ae02a is a highly secure and versatile hash function that has gained recognition for its strong resistance against various cryptanalytic attacks. Its wide range of potential applications, from digital signatures to cryptographic hashing, makes it a valuable tool for ensuring data integrity, security, and privacy in the digital age. As the demand for secure and efficient hash functions continues to grow, 20254ae02a is poised to play a significant role in shaping the future of cryptography.




Closure
Thus, we hope this article has provided valuable insights into 20254ae02a: Unveiling the Enigmatic Hash Function. We hope you find this article informative and beneficial. See you in our next article!
- 0
- By admin